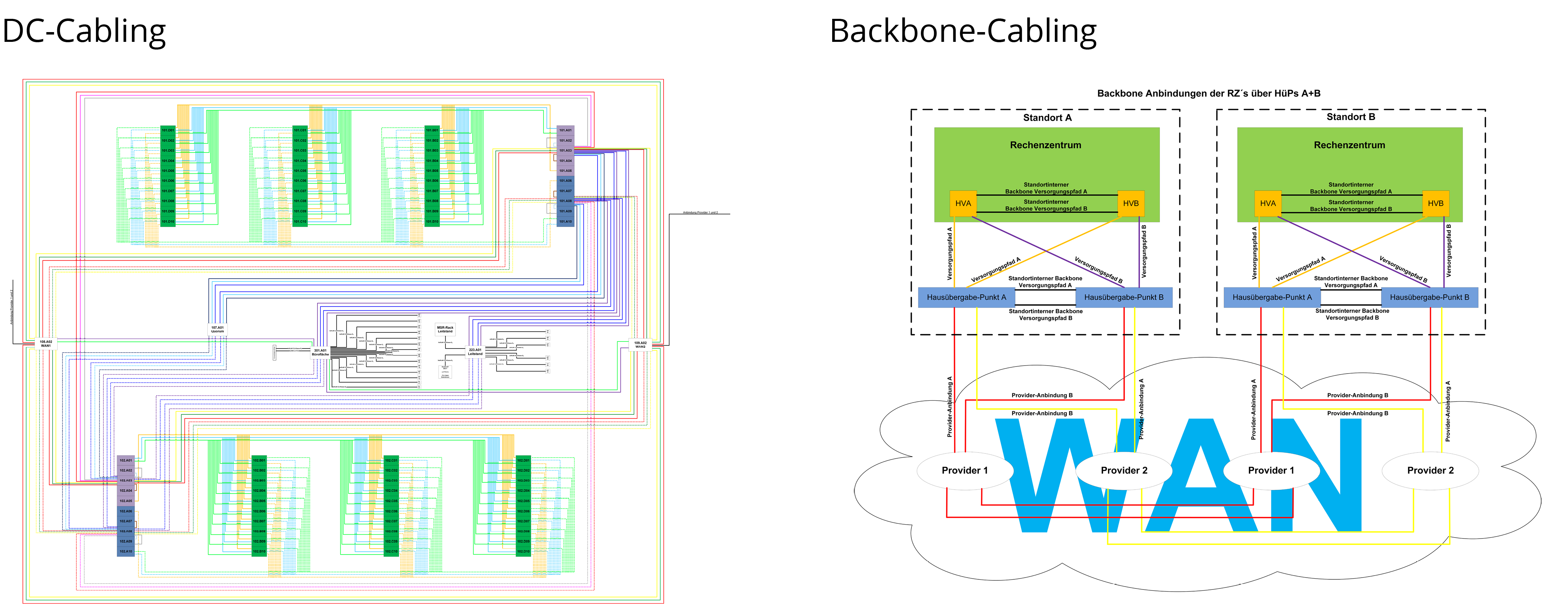
The infrastructure is the foundation of a secure and functioning IT & communication technology. But the security, quality and future orientation of a passive infrastructure often remains in the dark.
The most common reasons:
- Network infrastructures that have grown over several years
- Different quality levels
- Various technological standards
- Lack of clarity about future requirements
- Inadequate documentation
In four clearly structured steps, our analysis experts will give you answers to these questions:
Step 1: The actual recording | In the actual recording, we check the current network situation and the existing documentation. In this step, all communication links are traced – the first possible weaknesses can be identified.
Step 2: The protection needs assessment | Together with the user, we define the requirements potential for availability, redundancy, transmission parameters and ready-to-wear qualities. From this, we derive the key data for a comprehensive weak point analysis.